
A National Security Agency memo that recently resurfaced a few years after it was first published contains a detailed analysis of what very possibly was the world's first keylogger—a 1970s bug that Soviet spies implanted in US diplomats' IBM Selectric typewriters to monitor classified letters and memos.
The electromechanical implants were nothing short of an engineering marvel. The highly miniaturized series of circuits were stuffed into a metal bar that ran the length of the typewriter, making them invisible to the naked eye. The implant, which could only be seen using X-ray equipment, recorded the precise location of the little ball Selectric typewriters used to imprint a character on paper. With the exception of spaces, tabs, hyphens, and backspaces, the tiny devices had the ability to record every key press and transmit it back to Soviet spies in real time.
A “lucrative source of information”
The Soviet implants were discovered through the painstaking analysis of more than 10 tons' worth of equipment seized from US embassies and consulates and shipped back to the US. The implants were ultimately found inside 16 typewriters used from 1976 to 1984 at the US embassy in Moscow and the US consulate in Leningrad. The bugs went undetected for the entire eight-year span and only came to light following a tip from a US ally whose own embassy was the target of a similar eavesdropping operation.
"Despite the ambiguities in knowing what characters were typed, the typewriter attack against the US was a lucrative source of information for the Soviets," an NSA document, which was declassified several years ago, concluded. "It was difficult to quantify the damage to the US from this exploitation because it went on for such a long time." The NSA document was published here in 2012. Ars is reporting the document because it doesn't appear to have been widely covered before and generated a lively conversation Monday on the blog of encryption and security expert Bruce Schneier.
When the implant was first reported, one bugging expert cited in Discover magazine speculated that it worked by measuring minute differences in the time it took each character to be imprinted. That theory was based on the observation that the time the Selectric ball took to complete a rotation was different for each one. A low-tech listening device planted in the room would then transmit the sounds of a typing Selectric to a Soviet-operated computer that would reconstruct the series of key presses.
In fact, the implant was far more advanced and worked by measuring the movements of the "bail," which was the term analysts gave to the mechanical arms that controlled the pitch and rotation of the ball. According to the NSA document:
In reality, the movement of the bails determined which character had been typed because each character had a unique binary movement corresponding to the bails. The magnetic energy picked up by the sensors in the bar was converted into a digital electrical signal. The signals were compressed into a four-bit frequency select word. The bug was able to store up to eight four-bit characters. When the buffer was full, a transmitter in the bar sent the information out to Soviet sensors.
There was some ambiguity in determining which characters had been typed. NSA analysts using the laws of probability were able to figure out how the Soviets probably recovered text. Other factors which made it difficult to recover text included the following: The implant could not detect characters that were typed without the ball moving. If the typist pressed space, tab shift, or backspace, these characters were invisible to the implant. Since the ball did not move or tilt when the typist pressed hyphen because it was located at the ball’s home position, the bug could not read this character either.
The implants were also remarkable for the number of upgrades they received. Far from being a static device that was built once and then left to do its job, the bugs were constantly refined. The document says:
The Soviets continually upgraded and improved their implants. There were five varieties or generations of bugs. Three types of units operated using DC power and contained either eight, nine, or ten batteries. The other two types operated from AC power and had beacons to indicate whether the typewriter was turned on or off. Some of the units also had a modified on and off switch with a transformer, while others had a special coaxial screw with a spring and lug. The modified switch sent power to the implant. Since the battery-powered machines had their own internal source of power, the modified switch was not necessary. The special coaxial screw with a spring and lug connected the implant to the typewriter linkage, and this linkage was used as an antenna to transmit the information as it was being typed. Later battery-powered implants had a test point underneath an end screw. By removing the screw and inserting a probe, an individual could easily read battery voltage to see if the batteries were still active.
The ingenuity of the Soviets was remarkable because they did not merely move from batteries as a source of power to alternating current. There were early versions and later versions of bugs that used both sources of power. NSA found that the first three implants were battery powered. The first of these was shipped to Moscow in October 1976, and the other two were shipped in April of 1977. The first bug that used alternating current as its source of power was shipped to Moscow in November 1977. The remaining nine machines that were found in Moscow used alternating current as their source of power and were more advanced than the first AC-powered bug. Five of the advanced model AC bugged typewriters were delivered to Moscow in February 1982. The remainder were delivered in January of 1984. The later battery-powered bugged typewriters found in the consulate in Leningrad were shipped in April of 1977 and March of 1982.
All of the implants were quite sophisticated. Each implant had a magnetometer that converted the mechanical energy of key strokes into local magnetic disturbances. The electronics package in the implant responded to these disturbances, categorized the underlying data, and transmitted the results to a nearby listening post. Data were transmitted via radio frequency. The implant was enabled by remote control. Another advantage of these bugs was easy installation. Engineers estimated that a skilled technician could install an implant in a typewriter in a half hour. The integrated circuits were very sophisticated for that time period. The circuits contained one bit core memory, an advancement that NSA engineers had never seen.
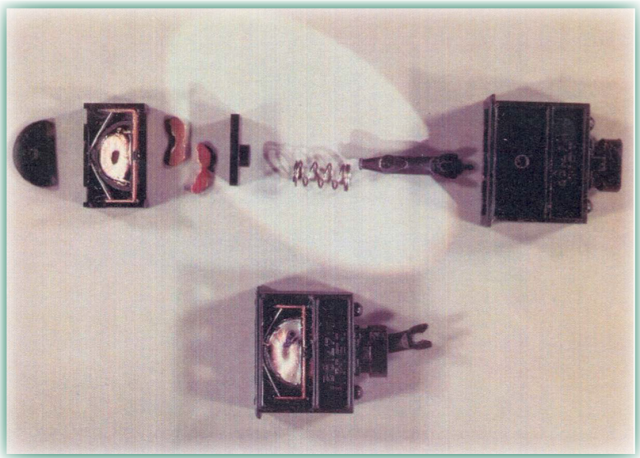
The devices could be turned off to avoid detection when the Soviets knew inspection teams were in close proximity. Newer devices operated by the US may have had the ability to detect the implants, but even then an element of luck would have been required, since the infected typewriter would have to be turned on, the bug would have to be turned on, and the analyzer would have to be tuned to the right frequency. To lower this risk, Soviet spies deliberately designed the devices to use the same frequency band as local television stations.
The account of "Project Gunman," which was the name given to the once-covert operation to discover and respond to the implants, underscores how drastically hacking has changed in the past 40 years.
"It's a lot easier now because everything is connected," Schneier, who is chief technology officer of Resilient Systems Inc., told Ars. "Everything is computerized and [that] makes it so much easier. When you just have to hack into somebody's computer, even if it's completely separate from the Internet, it's a much easier job, and that's why everybody can do it, including the criminals."
reader comments
90