iMessage 'denial-of-service' attack crashes devs' iOS Messages apps
A recent spate of prank texts sent to a group of iOS developers has revealed a limitation in how Apple handles data sent through its iMessage service, which in some cases can crash the app if the incoming message is too long or contains overly complex characters.
As reported to The Next Web, iOS app developers iH8sn0w, well known for his jailbreak tool, and Grant Paul were among those targeted by a type of denial of service (DoS) attack that overwhelmed their respective Messages inboxes with a load of automatically-generated transmissions.
The two devs believe the messages to have been sent one after another from the Messages app on OS X, with a simple AppleScript effecting the barrage that prompts a victim to constantly clear notifications and text.
“What’s happening is a simple flood: Apple doesn’t seem to limit how fast messages can be sent, so the attacker is able to send thousands of messages very quickly,†Paul said.
iH8sn0w mocked up a proof-of-concept AppleScript to demonstrate how such an attack may work. If Apple doesn't limit the influx of messages, a user's app will quickly become filled with what amounts to piles of spam.
As vexing as a continuous string of nonsense can be, a real issue arises when extraordinarily long or complex messages are received. This can cause Messages on iOS to crash because it can't process and display the massive amount of data correctly. According to the developers, the app will force itself to close and won't be able to re-open because it can't properly render the text.
While no surefire solution has been found to remedy a crashed Messages app, the publication suggests "playing around with sending a regular message, then locking the phone and activating the message notification until you’re able to time it right to delete the message thread that’s causing the problem." Paul effectively employed this method to delete the offending text and regain control of the app.
It should be noted that if an attacker gets ahold of a user's iMessage handle, the only option may be to disable that account temporarily. If a user's phone number is compromised, iMessage itself might have to be turned off.
The attacker's identity is unknown at this time, but the messages appear to have originated from a Twitter account used to sell UDIDs and provisioning profiles. Disposable email accounts were being used to send the spam, making it difficult to simply block the culprit as they can simply open another and continue the assault.
Apple has yet to issue a response to the recent development.
 Mikey Campbell
Mikey Campbell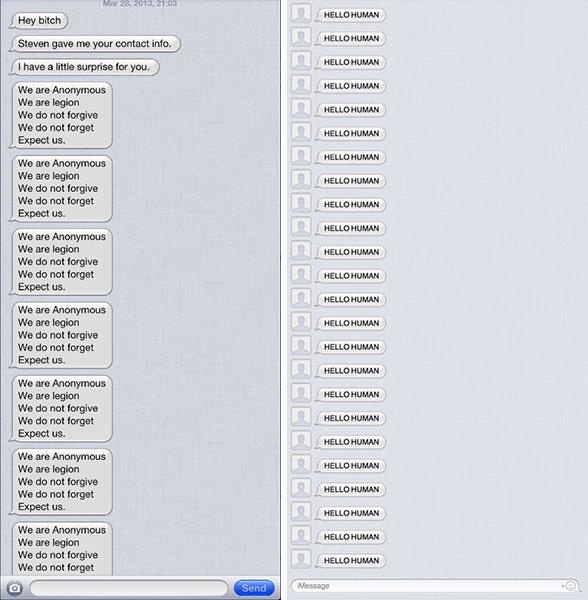











 Malcolm Owen
Malcolm Owen
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele
 Christine McKee
Christine McKee
 William Gallagher
William Gallagher
 Marko Zivkovic
Marko Zivkovic