Cisco: Cyber criminals keen on mobile device, cloud hacking

See also: Young professionals more willing to break IT rules: Cisco
As Cisco reported in June, most cyber criminals are dropping producing mass spam in favor of more targeted attacks.
"We're dealing with a much more professional criminal than we were dealing with before," said Cisco threat research manager Scott Olechowski, explaining that most cyber criminals are looking to make the most "bang for their buck" with the least risk.
The latest report goes further to explain how spam volume has dropped geographically. The United States, for example, was the number one source for spam in 2010, but it has since dropped to ninth place.
Instead, India is now the top origin for spam, followed by Vietnam, Russia, South Korea, and Indonesia.
Nevertheless, even if spam is rising in certain countries, that doesn't mean that spam is quite the same source of problems for Internet users as it was before. That's partially because more companies have sought out help from law enforcement and security officials, and some major global companies have had success. For example, Yahoo just won $610 million in a judgment over spammers.
Yet, Cisco reports that cyber crime has evolved to a much more sophisticated level with organized crime rings focused on bigger scams. For example, a cyber criminal might be more likely to use a phishing scam now to literally fish around for the easiest way into a wealthier account.
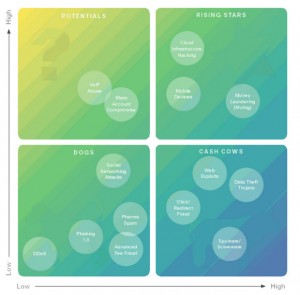
Cisco has divided major forms of cyber crime into four categories based on success and growth varying by scalability and revenue, as pictured in the diagram above.
Although it might be worrisome to many and provide quick justification to IT departments afraid of jumping into the cloud too quickly, mobile device and cloud infrastructure hacking are expected to be two of the biggest rising stars in cyber crime in 2012.
But the big targets are elsewhere, according to Cisco's report, which identifies spyware/scareware, data theft Trojans, click/redirect fraud, and web exploits as the biggest cash cows in cyber crime to come.
Basically, your personal identity is the most sought after, and most at risk, data in the minds of cyber criminals.
Related:
- Nearly half of college students prefer Internet to friends, dating (study)
- Cisco Gen-Y study: Mobile devices valued more than higher salaries
- Cisco rolls out IronPort Outbreak Filters, Business Class Email solutions
- Bring-your-own-device becoming accepted business practice (survey)
- Do-it-yourself apps becoming more popular with enterprises (report)