This new feature will make it tougher for cops and hackers to unlock your iPhone

(Screenshot: ZDNet)
There's a new twist in the long-running cat-and-mouse game between Apple and law enforcement.
A new feature, which first emerged in an early beta version of the company's iPhone and iPad software but never made it to market, has finally been released.
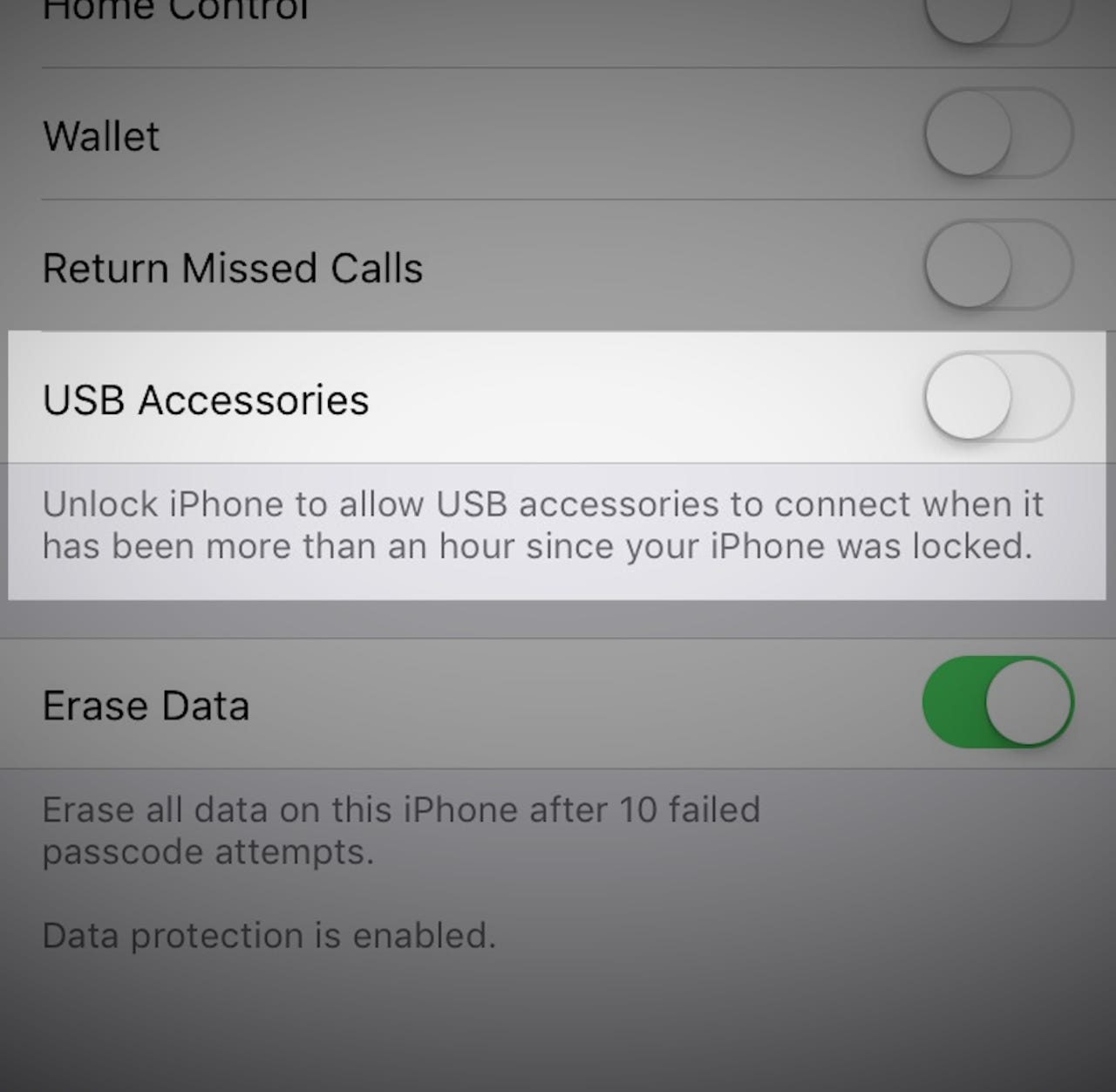
The latest version of the iPhone and iPad software, iOS 11.4.1, includes a new feature that requires users to unlock their device after an hour of inactivity to connect a USB accessory.
That's meant to make it more difficult for police -- and hackers -- to siphon all the data off a user's device.
The feature, called USB Restricted Mode, was first found in a beta version of iOS 11.3 in March, shortly after a new iPhone unlocking tool hit the market -- a device called GrayKey, which promises to help law enforcement unlock iPhones in a fraction of the time it usually takes.
The box, small enough to fit in your hand, uses an as-of-yet-unknown exploit that guesses the device's password again and again -- an attack known as brute-forcing -- to gain access to the iPhone's encrypted contents.
Apple introduced its so-called "zero-knowledge encryption" feature in iOS 8 in 2014, meaning only the device owner, and not Apple, can unlock the phone.
Law enforcement have long complained that they need access to locked devices to help with their investigations. But security experts have decried efforts by the government to lobby for backdoors, arguing that hackers could also get that same access and use it for their own gain.
The new feature doesn't require a code to recharge a device's battery.
It's the latest move in Apple's delicate balancing act of affording law enforcement some latitude in gaining access to locked iPhones, while trying to protect the rights of its users.
In recent software iterations, Apple introduced a change shutting down a device's Touch ID fingerprint sensor after two days. In the US, law enforcement can force you to use your fingerprint or scan your face to access and search your phone. That gives law enforcement long enough to unlock the phone if the person's finger is available. In some cases, police have used a dead person's fingerprint to access the contents of their phone.
But legal experts say that police may claim exigent circumstances and download the contents of a device without a warrant -- with the aim of obtaining one later, according to Riana Pfefferkorn, cryptography fellow at the Stanford Center for Internet and Society, in a blog post.
Apple has proactively contacted law enforcement to help in active investigations, ZDNet has previously reported. In the case of a shooter at a Texas church, Apple "immediately reached out to the FBI after learning from their press conference on Tuesday that investigators were trying to access a mobile phone," and "offered assistance and said we would expedite our response to any legal process they send us."
Updated: on July 9, with the arrival of USB Restricted Mode in iOS 11.4.1.