Eight days ago, the WCry ransomware worm attacked more than 200,000 computers in 150 countries. The outbreak prompted infected hospitals to turn away patients and shut down computers in banks and telecoms. Now that researchers have had time to analyze the self-replicating attack, they're learning details that shed new and sometimes surprising light on the world's biggest ransomware attack.
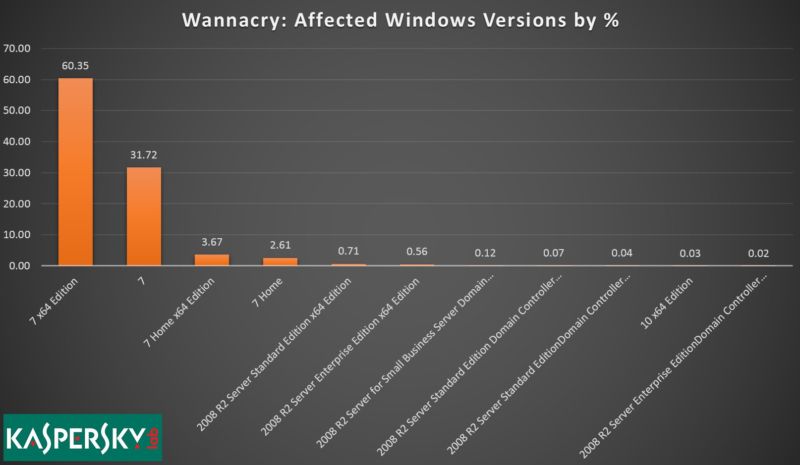
Chief among the revelations: more than 97 percent of infections hit computers running Windows 7, according to attacks seen by antivirus provider Kaspersky Lab. By contrast, infected Windows XP machines were practically non-existent, and those XP PCs that were compromised were likely manually infected by their owners for testing purposes. That's according to Costin Raiu, director of Kaspersky Lab's Global Research and Analysis Team, who spoke to Ars.
While the estimates are based only on computers that run Kaspersky software, as opposed to all computers on the Internet, there's little question Windows 7 was overwhelmingly affected by WCry, which is also known as "WannaCry" and "WannaCrypt." Security ratings firm BitSight found that 67 percent of infections hit Windows 7, Reuters reported.
The figures challenge the widely repeated perception that the outbreak was largely the result of end users who continued to deploy Windows XP, a Windows version Microsoft decommissioned three years ago. In fact, researchers now say, XP was largely untouched by last week's worm because PCs crashed before WCry could take hold. Instead, it now appears, the leading contributor to the virally spreading infection were Windows 7 machines that hadn't installed a critical security patch Microsoft issued in March
The Kaspersky figures are illuminating because they show Windows 7 x64 Edition, which is widely used by large organizations, being infected close to twice as much as Windows 7 versions mostly used in homes and small offices. It's not clear if that means enterprises are less likely to patch or if there are other explanations.
Don’t blame spam
Also on Friday, researchers published convincing evidence that malicious spam e-mails played no role in initially seeding last week's ransomware worm. Rather, according to a blog post published by AV provider Malwarebytes, it spread through a mechanism that scanned the Internet for computers with open Server Message Block ports. The worm then used a modified version of "EternalBlue,"—the advanced SMB exploit that was developed by the National Security Agency and leaked by the Shadow Brokers group—to install WCry on vulnerable computers. From there, WCry propagated from vulnerable machine to vulnerable machine inside local networks."Developing a well-crafted campaign to identify just... a few thousand vulnerable machines would allow for the widespread distribution of this malware on the scale and speed that we saw with this particular ransomware variant," Malwarebytes Senior Malware Intelligence Analyst Adam McNeil wrote.
A third revelation: more people than previously known may have been repackaging EternalBlue and other recently leaked NSA exploits in the weeks before the WCry outbreak. Security firm Secdo said on Friday that it unearthed evidence showing that multiple groups exploited the SMB vulnerabilities to install a separate ransomware package, steal login credentials, and to conscript computers into a botnet.
According to Secdo researcher Gil Barak:
Based on these findings, we suspect that the scope of the damage is much greater than previously thought and that there are at least three different groups that have been leveraging the NSA exploit to infect enterprise networks since late April... These attacks demonstrate that many endpoints may still be compromised despite having installed the latest security patch.
Researchers from a separate security firm already showed that criminals were using EternalBlue to make vulnerable computers part of a cryptocurrency mining botnet. A Secdo representative said the attacks the company reported occurred around the same time.
Meanwhile, EternalRocks—a separate self-replicating exploit also developed by the NSA and released in last month's Shadow Brokers release—is also being repackaged in active attacks. Researcher Miroslav Stampar has details here.
Finally, as reported by Wired on Friday, attackers have been using a knock-off of the powerful Mirai Internet-of-things botnet to attack two servers that are currently preventing WCry and a WCry copycat variant from spreading. Before executing on a vulnerable computer, the worms are programmed to reach out to hardcoded domain names. If the domains respond, the worm aborts without infecting or spreading. Researchers suspect developers intended the mechanism to function as a killswitch they could use to stop the worm, should attackers lose control of it. Should the distributed denial-of-service attacks knock the servers out of commission, there is the possibility the self-replicating infections could start again.
MalwareTech, the pseudonymous researcher who registered the domain that stopped last Friday's WCry worm, said he's not concerned about the attacks. He explained to Ars: "at this point, very few samples are actually spreading, so even if the sinkhole were to go offline, the damage would be limited."
Just to be on the safe side, he has sought the help of an unnamed DDoS mitigation service.
reader comments
194